Fight fraud by going deeper
An introduction to our fraud prevention tools Deep Email Check and Deep Phone Check
This article is an overview of how our fraud detection works.
For a more technical approach to why Defastra performs better than other anti-fraud solutions, we encourage you to read our various technical papers about disposable phone numbers & temporary emails.
Overview
Our approach to fraud prevention is simple but delves much deeper than other solutions, providing real-time, accurate, and detailed results.
Fighting fraud with us is transparent and straightforward:
- Simply submit a single phone number or email address using our manual tools, batch processing or API
- We gather real-time social & digital data about the email or phone submitted, also called data enrichment
- Our service runs a range of deep anti-fraud checks (click to see precisely what check we perform against phone numbers and against email addresses
- We return you all the data we gathered (from social media, data breaches, etc.) along with a
risk score&risk level, and an advanced yet easy-to-understand fraud report, including what risk or trust signals were discovered
In the next few sections of this article, we will go into detail about:
- How to interpret the risk level & risk score we generated
- What risk & trust signals are uncovered
- And what raw data will you also get
Risk level & risk score
Each deep check will return a risk score and a risk level.
- The risk score is a number between 0 (safe) and 100 (fraudulent).
- The risk level is our appreciation of the risk score.
There are 4 risk levels. Below you can see rough definitions of these risk levels, and our recommendations for each:
| Risk level | Description | Recommendation | Risk score range |
|---|---|---|---|
| low | No risk signals were uncovered and the phone or email appears to be safe. | Allow | 0 |
| medium | Some light risk signals were triggered. | Allow but flag | 1 - 20 |
| high | Serious risk signals were triggered, and we highly recommend security-sensitive businesses to block. | Allow and flag or block | 21 - 40 |
| extreme | The phone or email is fraudulent and triggered many definitive risk signals, always block. | Block | 40 - 100 |
Risk & trust signals explanation
The strength of our Deep Check tools lies in our carefully crafted fraud checks backed by AI, ratio surveillance, and years of analyzing fraud schemes.
Whenever you use our products, a list of checks will be run against your submitted element to find trust & risk signals, and uncover synthetical identities.
Our solution is fully transparent: each request will detail how the risk score was generated, along with all the signals we uncovered.
A signal can be:
- Risk: we uncovered a risky pattern
- Trust: we uncovered a trustworthy pattern
Each signal will also contain a detail property, giving you easy-to-read details about what we uncovered.
Here is an example of how a Deep Email Check result is displayed in our dashboard:
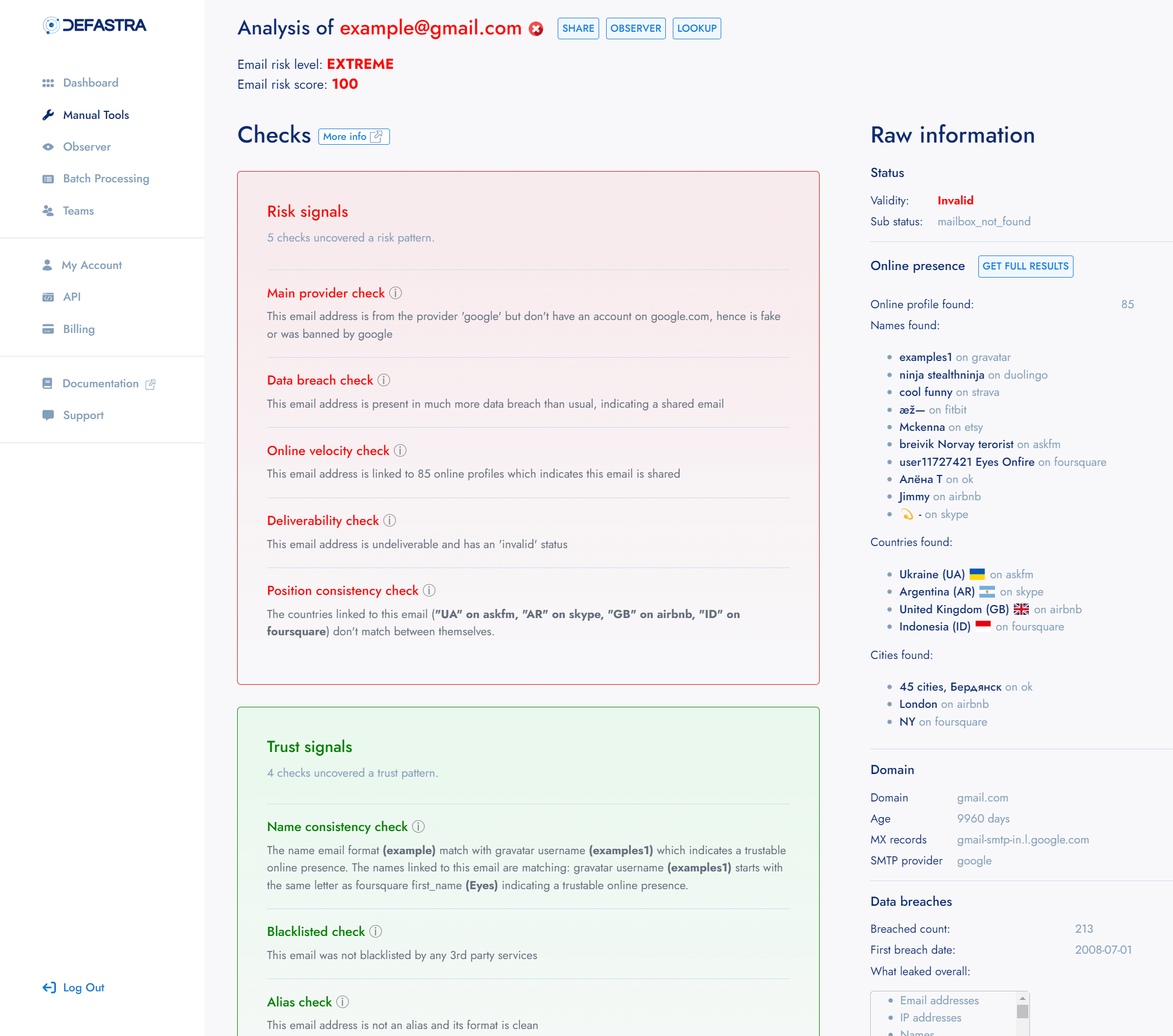
Example of Deep Email Check result
To deep-dive into what makes our Deep Check tools so efficient in uncovering fraudulent patterns and what powers them, check out our detailed Fraud checks list:
Note for API users
You can head to the API reference of the Deep Phone Check or Deep Email Check products and click on the example response result to see the
JSONrepresentation of a typical response.
Deep, yet simple
Each fraud check we perform drills deeply into the data associated with the phone number or email address provided, but delivers a simple and easily readable sentence that clearly says what happened.
Data enrichment
In addition to our risk analysis, we will also return exclusive social and digital data about the phone or email checked.
To find out what data we return, check our Up-to-date data list .
Updated almost 3 years ago
